Thales CipherTrust Manager
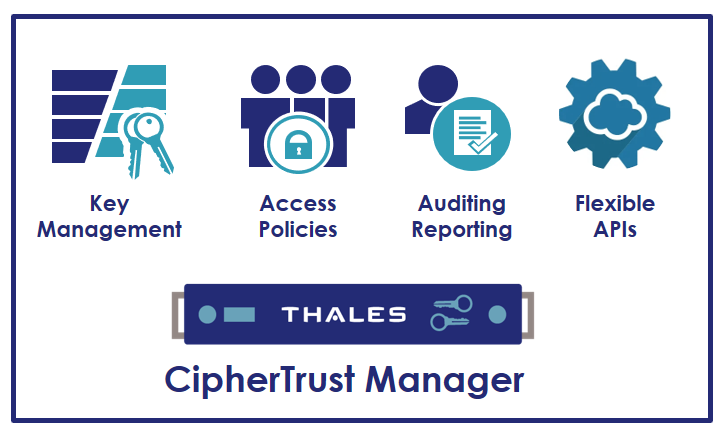
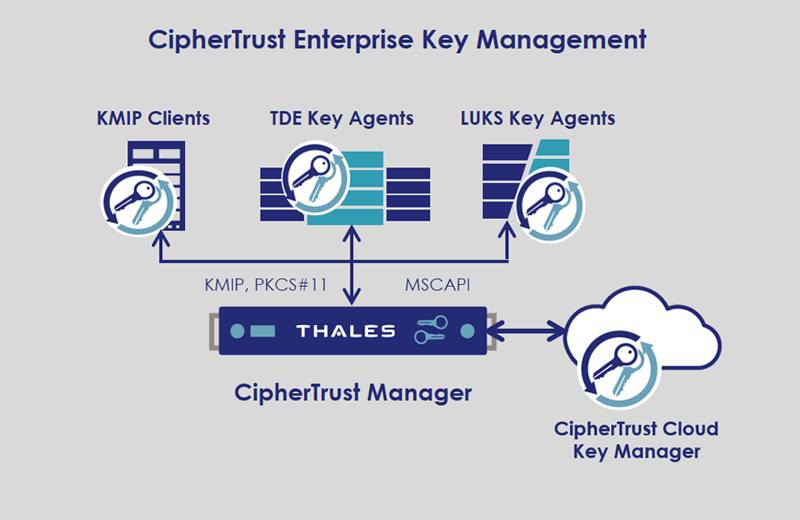
CipherTrust Manager enables organizations to centrally manage encryption keys for Thales CipherTrust Data Security Platform and third party products. It simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation, and deletion.
It provides role-based access control to keys and policies, multitenancy support, and robust auditing and reporting of all key management and encryption operations.
CipherTrust Manager is the central management point for the CipherTrust Data Security Platform. It provides a unified management console that makes it easy to discover and classify data, and to protect sensitive data wherever it resides using a comprehensive set of CipherTrust Data Protection Connectors from Thales.
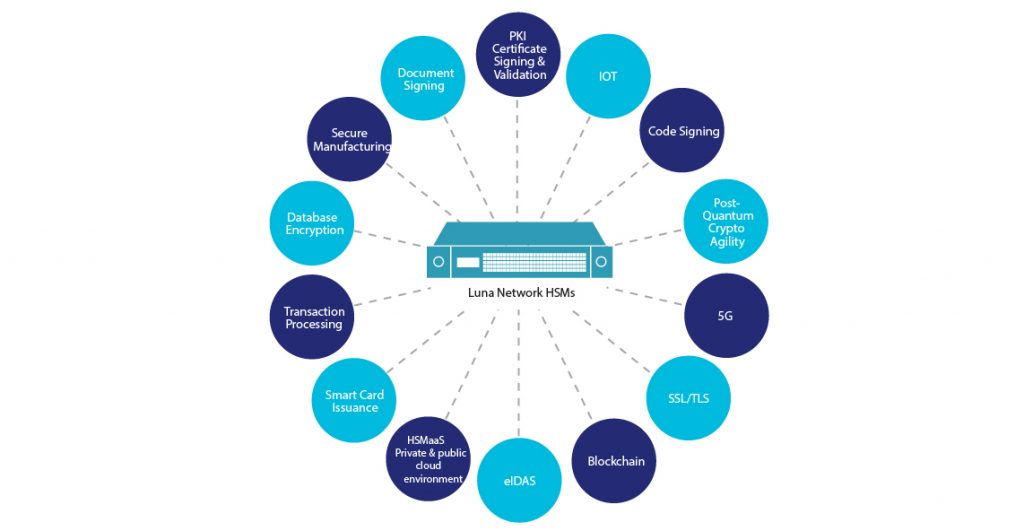
CipherTrust Manager is available in both virtual and physical form-factors that integrate with FIPS 140-2 validated Thales Luna Network or Cloud HSM, and third-party Hardware Security Modules (HSMs) for securely storing master keys with highest root of trust. These appliances can be deployed on-premises as well as in private or public cloud infrastructures. This allows customers to address compliance requirements, regulatory mandates and industry best practices for data security.
Benefits:
- Centralized key and policy management for on-premises data stores and cloud infrastructures
- Reduced business risk with unified data discovery, classification and sensitive data protection
- Simplified management with self-service licensing portal and visibility into licenses in use
- Cloud friendly deployment options with support for AWS, Azure, Google Cloud, VMware, Oracle Cloud Infrastructure and more
- Expanded Hardware Security Module (HSM) support for superior key control
- Unparalleled partner ecosystem of integrations with leading enterprise storage, server, database, application and SaaS vendors
Centralized Key Lifecycle Management
Simplifies management of encryption keys across their entire lifecycle, including secure key generation, backup/restore, clustering, deactivation and deletion. It unifies key management operations with role-based access control using existing Active Directory and LDAP credentials, and provides full audit log review.
Developer Friendly REST APIs
Offers new REST interfaces in addition to KMIP and NAE-XML APIs, for developers to simplify deployment of applications integrated with key management capabilities and automate testing and development of administrative operations.
Unified Management Console
Provides a single pane of glass for the CipherTrust Data Security Platform products, that enable organizations to discover, classify, and encrypt or tokenize data to reduce business risk and satisfy compliance regulations. It streamlines provisioning of connector licenses through a new self-service licensing for better visibility and control of licenses.



 ไทย
ไทย